Misc PCI Requirements
Please use these as ticklers to yourself.
 |
If card data is to be transmitted over a public network (i.e. outside your firewall), it must be sent using secure encryption technology like IPSEC, VPN or via TLS per PCI DSS 4.1. |
 |
Do not send any credit card data 'in the clear' such as pasting a card number into an email, or into an IM per PCI DSS 4.2 unless you are using secure encryption with these messaging technologies. Do not encourage customers to send card numbers, CVV2 numbers, name, expiry dates, or any other such data to you via the same technologies.
|
 |
If you are upgrading from a prior system that might have had unencrypted credit card information, you must throw that data into the trash and secure erase it with a tool like ERASER (free) on the PC or use File Menu -> Secure Erase on Mac. |
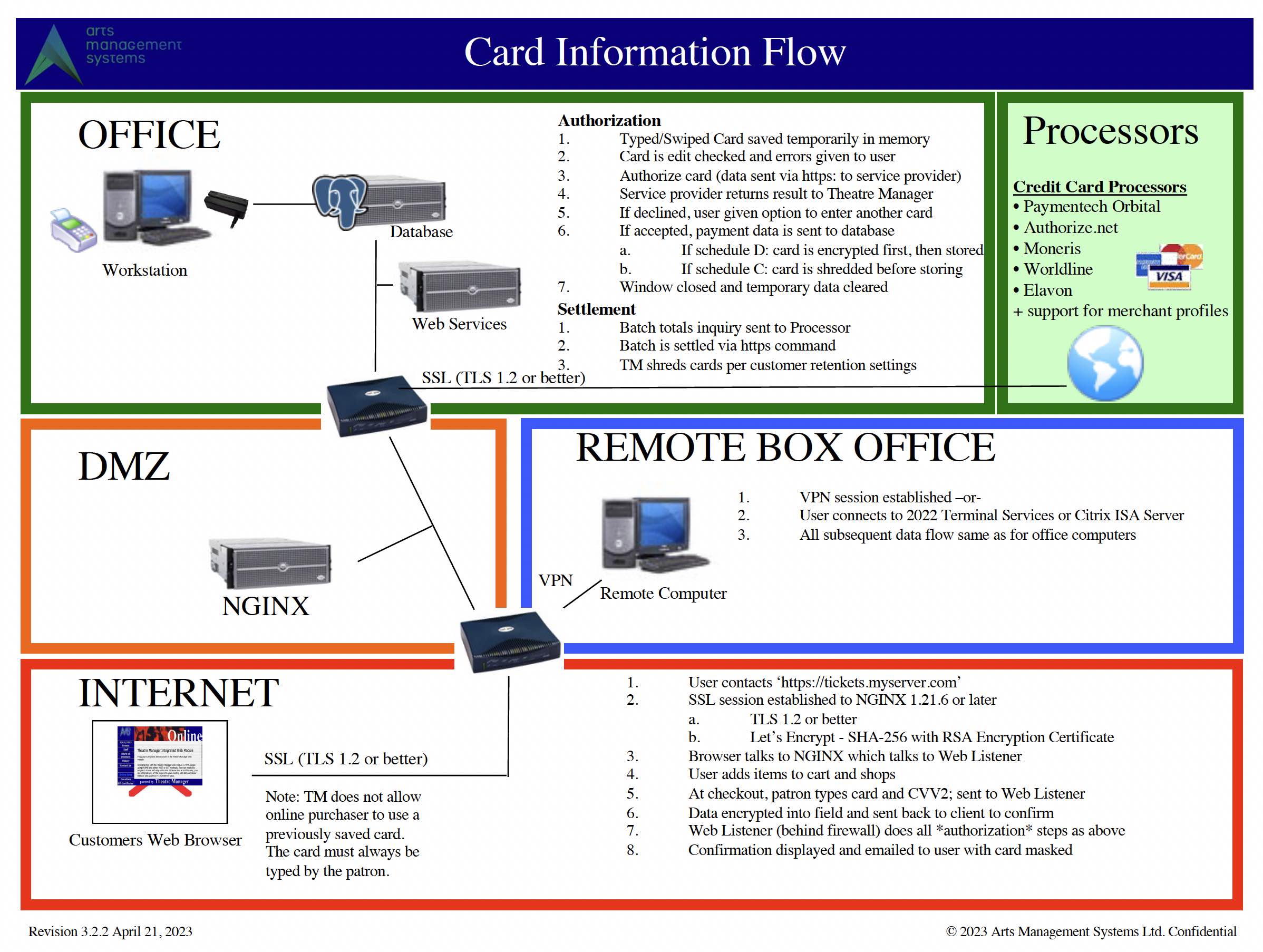
Card Flow Across System
(Click to enlarge as a PDF)
Vulnerability Identification and Assessment
 |
PCI requires that a venue establish a listing of security vulnerabilities and track them in a database as well as implement programs to prevent vulnerabilities PCI requirement 6.2.
Common Vulnerabilities and Exposures (CVE) vulnerabilities are reviewed at least monthly. As standard practice, Arts Management considers all CVE's to be a high priority for the software we incorporate. As such, these will be implemented using the auto deployment processes (regardless if they really affect Theatre Manager or not) under the principle of better to be safe than sorry. The release notes may mention any important fixes felt to be applicable. We provide a list of vulnerabilities & patches specific to Theatre Manager and its components and update our installers regularly to address known issues. |
Addressing PCI compliance and preventing most security issues is as simple as:
- Keeping Theatre Manager up to date with the latest version (this occurs automatically via the auto deployment systems)
- Updating all operating systems to current updates from the vendor
- Having current anti-virus software in place
However, this is only one aspect of protecting your network. It is far more likely that vulnerabilities will arise from other programs. Here are some links that might be of interest to you to help maintain the health of your computers and networks.
| Item | Purpose |
| NIST.gov | This web site has a list of recent security issues from the government web site. It is useful for seeing if there is something pertinent to your software suite. This is worth searching on a periodic basis. |
| NIST.org | This web site has a summary of common security fixes and patches distilled from the government web site. |
|
Secunia
PC only |
PC's are vulnerable in a number of ways. Secuia is a free tool (for personal use) that inspects your PC and tells you about any vulnerabilities you may have on your PC that you are unaware of, and will automatically update versions of other software.
Note: Never forget to have anti-virus software on your machine. |
| Software Update Mac Only | macOS has a software update feature for the operating system. For workstations, we recommend automatically applying security patches. |
| OSVDB | This is an open source vulnerabilities database. We look at this periodically to see if there is anything that might affect tools that we supply to you. Apache and Postgres are both open source, so this is of interest to us. You may find other information, especially if you are using many open source tools. |
| QUALYS Labs | Use this to verify if a TLS Certificate is setup right and if system scans are looking for new vulnerabilities |
NGINX Vulnerability List
 |
Nginx is auto deployed with each version of TM server. It will always have the latest vulnerabilities mitigated per release notes and all attempts are made to deliver it within the mandated PCI time frame of 30 days of release (subject to testing and evaluation of other fixes). Typical time to deployment is within 15 days. |
Postgres Vulnerability List
|
The Theatre Manager postgres installers are always updated to the most recent version of postgres as soon possible after the postgres version it is released, ensuring any vulnerabilities are addressed by Arts Management as soon as a fix is released by the Postgres foundation. |
Postgres vulnerabilities are monitored on the Postgres Security web site.
Those immediately relevant to Theatre Manager are listed with the release notes for that version of Theatre Manager and may require a forced update to the database server before an update to Theatre Manager will allow connection to the server.
OWASP and Theatre Manager
The OWASP Top 10 for 2021 is interesting reading for application developers, web site builders, and end users. The internet has many good features, but it is not a safe place if you are not aware.
 |
Each year, the Arts Management team reviews the top 10 and, for those that are applicable, ensures that the web sales module provides a defence against the top 10 per PCI standard 6.5. Requirements are posted here. Merchants should also be aware of these. |
 |
In addition, please be aware that IFRAMES are disabled in NGINX due to possibility of a Click-Jacking attack. An iframe has typically been used by people (like MOGO Interactive) selling marketing pixels to include their code in your web site. PCI council checks for Click Jacking opportunity - so we have disabled this in our standard web Server Setup. |
2021 Top 10 List
| Description | Theatre Manager Implementation | |
2021A01 2017A05 |
Broken Access Control |
Access control enforces policy such that users cannot act outside of their intended permissions. Failures typically lead to unauthorized information disclosure, modification, or destruction of all data or performing a business function outside the user's limits
|
2021A02 2017A03 2015A06 2013A06 |
Cryptographic Failures | Many web applications do not properly protect sensitive data, such as credit cards, tax IDs, and authentication credentials. Attackers may steal or modify such weakly protected data to conduct credit card fraud, identity theft, or other crimes. Sensitive data deserves extra protection such as encryption at rest or in transit, as well as special precautions when exchanged with the browser.
Theatre Manager handles encryption of the key card information and recommends shredding of unused data after a period of time. All credit card information is re-encrypted on a periodic basis per PCI compliance and the only information retained is per PCI standards. Theatre Manager web services use TLS for all traffic, which means using port 443 to the NGINX server, and having a valid TLS certificate. Ensuring the TLS certificate is current is a responsibility of the monthly PCI scan process, and we contact customers when they are ready to expire. Users are encouraged to define a card retention period where TM will automatically shred cards based on their policy. |
2021A03 2017A01 2015A01 2013A01 |
Injection | Injection flaws, such as SQL, OS, and LDAP injection occur when untrusted data is sent to an interpreter as part of a command or query. The attacker’s hostile data can trick the interpreter into executing unintended commands or accessing data without proper authorization.
OWASP's preferred option is to use a safe API which avoids the use of the interpreter entirely or provides a parameterized interface. In Theatre Manager, all web pages access the web listener using a parameterized API (generally html form) and each parameter is scrubbed on the way to the web listener for specific values. Only acceptable parameters are verified. Unacceptable parameters are rejected and ignored. |
2021A04 |
Insecure Design |
Insecure design is a broad category representing different weaknesses, expressed as "missing or ineffective control design."
|
2021A05 2017A06 2015A05 2013A05 |
Security Misconfiguration | Good security requires having a secure configuration defined and deployed for the application, frameworks, application server, web server, database server, and platform. Secure settings should be defined, implemented, and maintained, as defaults are often insecure. Additionally, software should be kept up to date.
The primary preventative measure for this is PCI security scans and upgrading of Theatre Manager components on a regular basis and following any implementation notes. Users are encouraged to install operating system upgrades as they are made available and to turn on automatic checking on all workstations. On servers, the practice is to verify weekly for updates and install on a controlled basis. Theatre Manager regularly offers the latest updates to web servers and TLS security patches when they are made available. Configuration files are hardened as vulnerabilities are detected (example: preventing directory listings is the default browser config). |
2021A06 2017A09 2015A09 2013A09 |
Vulnerable and Outdated Components | Components, such as libraries, frameworks, and other software modules, almost always run with full privileges. If a vulnerable component is exploited, such an attack can facilitate serious data loss or server takeover. Applications using components with known vulnerabilities may undermine application defenses and enable a range of possible attacks and impacts.
Theatre Manager is designed to detect the version of significant components and will not start if the database version, web server version, or other significant components are insufficiently current. Most importantly, TM Web Servers are regularly updated with security patches. |
2021A07 2017A02 2015A02 2013A02 |
Identification and Authentication Failures | Application functions related to authentication and session management are often not implemented correctly, allowing attackers to compromise passwords, keys, or session tokens, or to exploit other implementation flaws to assume other users’ identities.
Theatre Manager uses cookies for session management. All data in the cookie is AES256 encrypted, along with a date and time. If the web listener notices that the cookie comes back and contains an unexpected date and time setting, then it discards the request and resets the user. There are no session IDs in any URL. |
2021A08 |
Software and Data Integrity Failures |
Software and data integrity failures relate to code and infrastructure that does not protect against integrity violations.
|
2021A09 2017A10 |
Security Logging and Monitoring Failures |
Security Logging and Monitoring Failures is to help detect, escalate, and respond to active breaches. Without logging and monitoring, breaches cannot be detected.
|
2021A10 |
Server-Side Request Forgery (SSRF) |
SSRF flaws occur whenever a web application is fetching a remote resource without validating the user-supplied URL. It allows an attacker to coerce the application to send a crafted request to an unexpected destination, even when protected by a firewall, VPN, or another type of network access control list (ACL).
|
| ------- | Historical References |
--------
|
2021MGD 2017A04 |
XML External Entities (XXE) 2021 merged with A05-Security Misconfiguration |
Many older or poorly configured XML processors evaluate external entity references within XML
documents. External entities can be used to disclose internal files using the file URI handler,
internal file shares, internal port scanning, remote code execution, and denial of service attacks.
|
2021MGD 2017A07 2015A03 2013A03 |
Cross-Site Scripting (XSS) 2021 merged into A03-Injection |
XSS flaws occur whenever an application takes untrusted data and sends it to a web browser without proper validation or escaping. XSS allows attackers to execute scripts in the victim’s browser which can hijack user sessions, deface web sites, or redirect the user to malicious sites.
OWASP's preferred option is to properly escape all untrusted data based on the HTML context (body, attribute, JavaScript, CSS, or URL) that the data will be placed into. Theatre Manager looks for any attempt to put Javascript and other characters into a form and simply removes them. We have determined that there is no valid need to have words like <script> in enterable fields like name or address. |
2021MGD 2017A08 |
Insecure Deserialization 2021 merged into A08-Software and Data Integrity Failures |
Insecure deserialization often leads to remote code execution. Even if deserialization flaws do not
result in remote code execution, they can be used to perform attacks, including replay attacks,
injection attacks, and privilege escalation attacks.
|
2017MGD 2015A04 2013A04 |
Insecure Direct Object References 2017 merged into A05-Broken Access Control |
A direct object reference occurs when a developer exposes a reference to an internal implementation object, such as a file, directory, or database key. Without an access control check or other protection, attackers can manipulate these references to access unauthorized data.
Theatre Manage does not allow direct access to any object in the database through the use of an API. Users cannot retrieve data in an unauthorized way as all queries are done via a controlled API. |
2017MGD 2015A07 2013A07 |
Missing Function Level Access Control 2017 merged into A05-Broken Access Control |
Most web applications verify function level access rights before making that functionality visible in the UI. However, applications need to perform the same access control checks on the server when each function is accessed. If requests are not verified, attackers will be able to forge requests in order to access functionality without proper authorization.
This does not directly apply to Theatre Manager's web services due to the APIs used to control access to the system -AND- the very limited number of pages in the WebPages directory which are used exclusively for the singular function of web sales. Accessing the limited number of web pages in the WebPages directory in a direct manner does nothing unless they are processed by a web service. |
2017n/a 2015A08 2013A08 |
Cross-Site Request Forgery (CSRF) | A CSRF attack forces a logged-on victim’s browser to send a forged HTTP request, including the victim’s session cookie and any other automatically included authentication information, to a vulnerable web application. This allows the attacker to force the victim’s browser to generate requests the vulnerable application thinks are legitimate requests from the victim.
Theatre Manager does not allow access to the database except via API. It also forces a timeout for inactivity and injects a unique form token key for each HTTP POST request. The cookie is time sensitive and is unique for each request sent from the server and back from the client. It is encrypted and contains other non-visible data that must be verified upon receipt back at the server. Failure to meet the verification requirements causes rejection of the request and the process to start over. Absence of a properly formatted and encrypted cookie rejects the request and starts over. The form token is a unique encrypted time-sensitive field that is placed into each web page by the server. When a form is submitted, the server checks the form token with what was sent out. If it does not match, the patron is sent to a 'safe' landing page. Currently, Theatre Manager sends patrons who are logged in to the 'home' page and those that are browsing anonymously to the 'event listing' page. No form can be submitted twice. |
2017n/a 2015A10 2013A10 |
Unvalidated Redirects and Forwards |
Web applications frequently redirect and forward users to other pages and websites, and use untrusted data to determine the destination pages. Without proper validation, attackers can redirect victims to phishing or malware sites, or use forwards to access unauthorized pages.
Theatre Manager does not use redirects to any unknown source in any commerce web page. All URLs returned by the server are specific to each API. Requests for APIs that do not exist return a proper 404 HTTP response (not found) |